Title: The Last Day of a Scammer: How Using Real Names Exposed a Fraudulent Operation
Introduction
In the ongoing battle against cybercrime, few moments are as satisfying as witnessing a scammer's operation unravel from the inside. A recent video from cybersecurity advocate Jim Browning provides a rare and revealing look into the final moments of a scam call center employee, captured through CCTV footage. Titled "CCTV of using a scammers' real names," the video not only entertains but educates viewers on the tactics used to disrupt these illegal operations. This post breaks down the key takeaways from the video and discusses how public awareness and proactive measures can help combat such scams.
Main Content
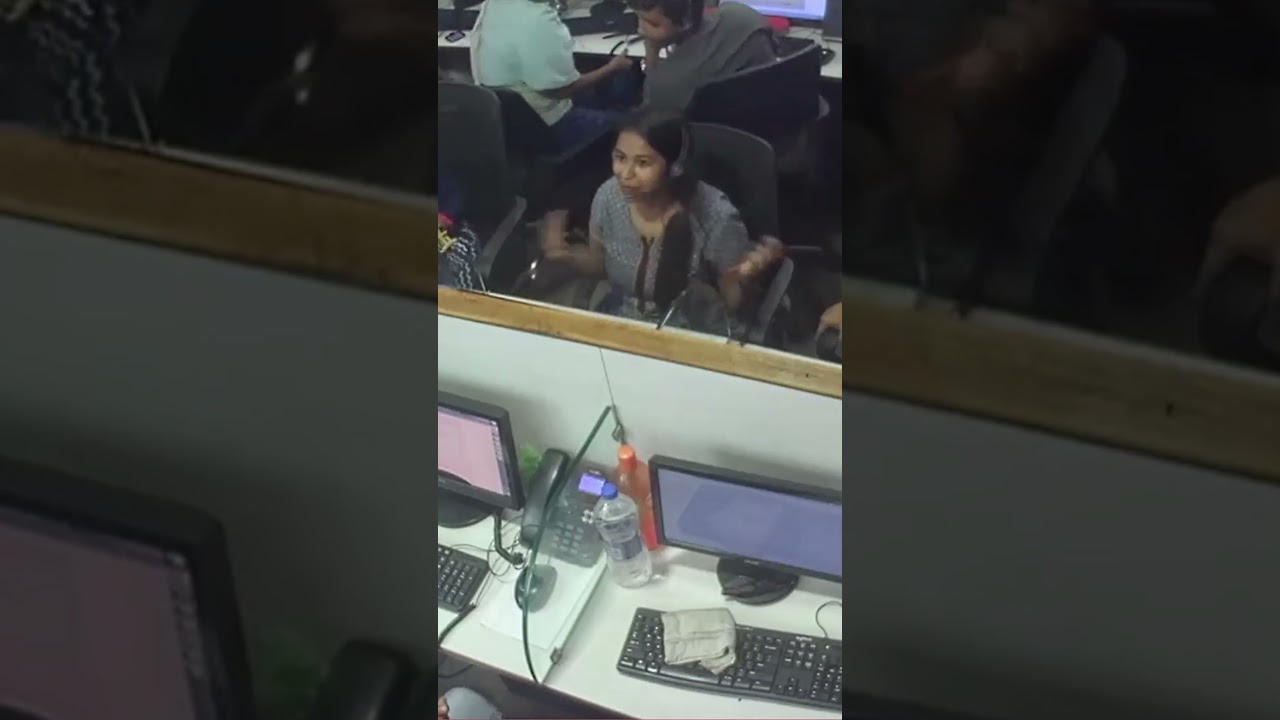
The video centers on an individual referred to as "Poor Pryia," whose last day at a fraudulent call center is documented through surveillance footage. Jim Browning, known for his work in hacking back against scammers, managed to access the CCTV feed, providing an unprecedented glimpse into the inner workings of these criminal enterprises. The title hints at one of Browning's signature techniques: using the real names of scammers to disrupt their operations and expose their identities.
Scammers often hide behind pseudonyms and spoofed numbers, creating a veil of anonymity that makes them difficult to trace. By uncovering and using their real names, Browning and others like him introduce a level of accountability that scammers fear. This approach not only halts individual scams but can also lead to the dismantling of entire call centers, as seen in the video.
The footage shows the chaos and tension that ensue when scammers realize their cover is blown. Employees are seen scrambling, managers are agitated, and the usual scripted deceptions fall apart. This serves as a powerful reminder that these operations are not invincible; they can be disrupted with the right information and tactics.
For the general public, the video underscores the importance of vigilance. Microsoft-themed scams, in which fraudsters impersonate tech support agents, remain prevalent. These scammers often use fear and urgency to manipulate victims into granting remote access or paying for unnecessary services. Recognizing these red flags—such as unsolicited calls, requests for personal information, or demands for payment via gift cards—can help potential targets avoid falling victim.
Conclusion
Jim Browning's video offers more than just a humorous look at a scammer's bad day; it provides valuable insights into how cybercriminals operate and how they can be stopped. By leveraging real names and other identifying information, ethical hackers like Browning are making it increasingly difficult for these fraudsters to hide.
Raising public awareness is crucial in the fight against scams. Educating yourself and others on common tactics, verifying the identity of anyone requesting sensitive information, and reporting suspicious activity to authorities are all effective ways to contribute.
If you found this information helpful, consider supporting Jim Browning's work through Patreon or Buy Me a Coffee, as linked in the video description. Follow him on social media for ongoing updates and tips on staying safe online.
Together, we can help expose and eliminate these fraudulent operations, one scammer at a time.
This post was generated from the YouTube video: CCTV of using a scammers' real names #funny #scammer #microsoft #cctv by Jim Browning