The most meaningful upgrades no longer shout. They arrive as thinner lines, quieter interfaces, and choices that remove friction instead of adding features. Beneath the polished surface, however, a different kind of redesign is taking place: systems are being rebuilt to protect data, identities, and trust by default. A smarter upgrade now pairs sleek design with stronger security-less visible, more deliberate. This alignment is not accidental. Minimalist hardware reduces ports and seams; streamlined software trims menus and prompts. Both can narrow the paths for error and attack. At the same time, modern threats demand defenses that are embedded rather than bolted on: hardware roots of trust, on-device processing, passkeys in place of passwords, authentication that adapts without interrupting. The result aims for an experience that feels effortless precisely because the difficult work is happening out of sight. This article looks at how form and protection are being co-designed-where simplicity supports safety, where it risks oversimplifying, and what signals indicate that “sleek” is more than cosmetic. It examines the trade-offs, the quiet technologies behind them, and practical ways to evaluate whether an upgrade is truly smarter, not just newer.
Sleek design with purpose: slimmer bezels, tactile materials, accessible layouts that reduce cognitive load
Form follows attention. Thinner borders quiet the edges so content breathes, making the device feel compact without shrinking the view. Finely grained, low-gloss finishes and softly knurled edges give your fingers landmarks, turning every swipe and press into a confident, repeatable gesture. Materials earn their keep-recycled aluminum, ceramic-infused coatings, and plant-derived polymers-balancing durability with a calm, tactile presence. The aesthetic is restraint: fewer lines, fewer seams, more signal.
- Thin borders: bigger canvas, fewer distractions
- Tactile edges: orientation without looking
- Low‑glare textures: softer reflections, less eye fatigue
- Subtle haptics: quiet confirmation you can feel
Clarity continues in the interface. Layouts are tuned to reduce decision friction-consistent navigation zones, generous spacing, readable type that scales, and color that guides rather than shouts. Each screen favors one primary action, pairs icons with labels for quick parsing, and uses progressive disclosure to pace information. The result is an accessible rhythm: predictable patterns, thumb‑friendly targets, and content grouped in digestible steps.
| Design cue | Why it helps |
|---|---|
| Whitespace | Faster scanning |
| Consistent placement | Less relearning |
| Readable type | Lower eye strain |
| Large targets | Fewer mistakes |
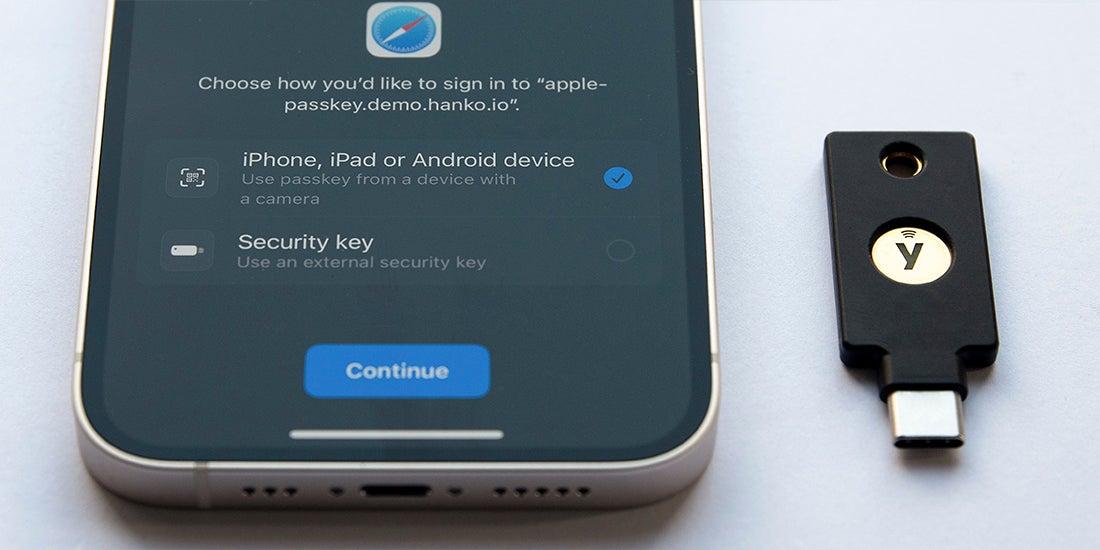
Stronger security by default: adopt passkeys, enable biometric unlock with on device encryption, require hardware backed keys
Goodbye, brittle passwords; hello, seamless sign‑in. With passkeys, your identity is proven by a cryptographic handshake that lives on your device, guarded by biometric unlock and sealed with on‑device encryption. The private half of the key never leaves its secure hardware enclave, so there’s nothing for phishers to steal and nothing to type. Whether you tap a finger, glance at the camera, or use a trusted security chip, access becomes instant, private, and resilient against SIM swaps, credential stuffing, and replay attacks.
- Passkeys: One‑tap, phishing‑resistant sign‑in-no codes, no guesswork.
- Biometric unlock: Face or fingerprint stays local; raw data never touches the cloud.
- Hardware protection: Keys generated and stored in secure silicon (TPM/Secure Enclave) with attestation.
| Scenario | What happens | Experience |
|---|---|---|
| Sign in | Cryptographic challenge | Tap and go |
| Unlock vault | Local biometric match | No typing |
| Approve payment | Hardware attestation | Confident, quick |
For teams and power users, default‑on policies make security effortless: require hardware‑backed keys for new enrollments, gate sensitive actions behind biometrics, and keep secrets encrypted at rest on the device. Compatibility with modern standards (FIDO2/WebAuthn) ensures smooth rollouts, while sensible recovery-like physical security keys or verified device pairs-keeps lockouts rare without weakening defenses. The result is a cleaner flow, fewer resets, and protection that scales quietly in the background.

Privacy that works in the background: keep processing on device, apply differential privacy, minimize data retention and third party sharing
Security should be seamless, not a trade-off. Our intelligence runs at the edge, turning your device into a private workspace where sensitive tasks-from photo categorization to voice actions-happen locally. Differential privacy adds carefully calibrated noise to aggregate metrics, protecting individual signals while preserving insight. That means helpful features keep learning without peeking at your personal world.
- On-device compute: models execute locally, reducing exposure and network dependency.
- Hardware-backed protection: keys and biometric data stay inside secure enclaves.
- Noise for anonymity: aggregated trends are shielded with differential privacy.
- Network restraint: only essential, de-identified summaries leave the device.
| Data Type | Default Flow | Retention | Third-Party Sharing |
|---|---|---|---|
| Photo recognition | Local only | Ephemeral | None |
| Keyboard insights | Aggregated, noisy | Rolling window | None |
| Crash diagnostics | Opt-in, redacted | Short-term | None |
Minimalism guides our data lifecycle: collect less, keep it briefly, and share sparingly. Clear controls put you at the helm, with transparency that’s readable at a glance. You decide what’s stored, what’s learned, and what’s forgotten-no detective work required.
- One-tap controls: toggle analytics, permissions, and backups from a single panel.
- Auto-expiry: time-based deletion for caches, logs, and tokens.
- Export and erase: download your footprint or wipe it entirely.
- Plain-language logs: see what ran, when it ran, and why-without jargon.
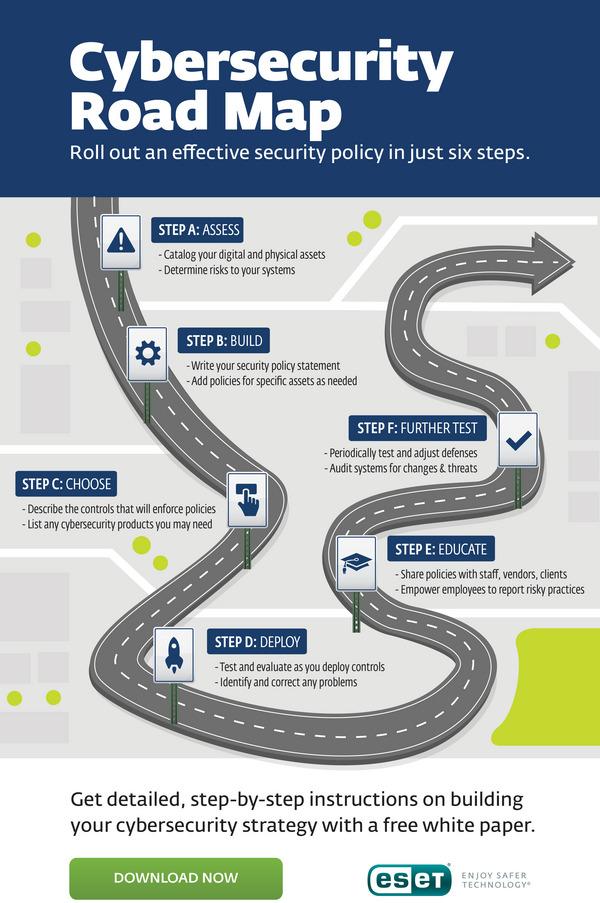
A practical upgrade roadmap: patch critical vulnerabilities first, phase rollout by risk and user impact, track MTTR and adoption to iterate
Neutralize the biggest risks first-close actively exploited CVEs, internet‑facing weaknesses, and privilege escalations-then expand change carefully. Roll out in rings with explicit entry/exit criteria, sequencing cohorts by their exposure and business sensitivity. Keep the experience sleek and reversible: use feature flags, preflight health checks, and a one-step rollback so every move is observable, pause‑able, and easy to unwind without disrupting work.
- Triage rules: exploits-in-the-wild → externally exposed → lateral-movement/priv‑esc → noisy but low-risk UX fixes.
- Ring order: Ring 0 (IT/Sec) → Ring 1 (product champions) → Ring 2+ (departments by risk and usage patterns).
- Safeguards: health probes, error budgets, auto-hold on SLO breach, documented rollback recipes.
- Timing & comms: timezone-aware windows, avoid revenue peaks, concise “what changes and why” notes.
| Ring | Scope | Change window | Primary KPI |
|---|---|---|---|
| 0 | IT + Security | Off‑peak | Smoke pass < 15m |
| 1 | Champions | Low‑peak | Crash < 0.5% |
| 2 | Broad | Regional off‑peak | Adoption > 80% (7d) |
| E | Exceptions | Approved slot | Waiver OK |
Iterate by evidence: pair engineering telemetry with human signals to watch MTTR and adoption in real time. Define guardrails (alerts, auto‑pause on regression), compare cohorts, and fold what you learn back into the next wave-reprioritize the patch queue, refine comms and in‑app cues, and tune defaults so security tightens as friction falls.
- MTTR: time from detection to fix and verified recovery.
- Adoption curve: 1/7/30‑day uptake, opt‑out rate.
- Stability: failure/rollback rate, error budget spend.
- Support load: tickets per 100 users, first‑contact resolution.
- Enablement: time‑to‑educate (guide views → task completion).
- Governance: exception backlog age, review outcomes.
In Conclusion
In the end, a smarter upgrade isn’t a louder one. It’s a quieter confidence: design that recedes, security that steadies, and both working without spectacle. Whether it’s worth the leap depends on what you notice and what you need, but the direction is clear-cleaner lines, calmer interactions, and safeguards that travel with you instead of standing in your way. It feels less like a finish line than a better baseline. From here, the proof will live in the margins: updates, disclosures, and everyday use. If the balance holds, sleek and secure won’t be opposites anymore-they’ll be the same surface.