The phone rings the way it always does-same vibration, same chime-yet what waits on the other end is rarely as ordinary. A voice introduces itself with calm authority, an automated message warns of account irregularities, a friendly stranger offers a windfall delayed only by a small verification step. The script varies, the cadence shifts, the number flashes and flickers through spoofed identities, but the choreography is remarkably consistent: a call arrives, a story unfolds, and a decision is pressed into the narrow space of a few urgent seconds.
Scam phone calls sit at the intersection of technology and psychology. They borrow the credibility of familiar institutions, the rhythms of customer service, the intimacy of a direct conversation. They thrive on gaps-gaps in information, in attention, in digital literacy-and they exploit the way phones still feel personal, even as they’ve become just another node in a vast, automated network.
This article examines the mechanics behind these calls: how they find us, how they frame their requests, and why certain tactics keep working. It also explores the tools designed to filter them out, the laws that attempt to constrain them, and the simple habits that shift the odds in our favor. No panic, no paranoia-just a clearer picture of a persistent, evolving persuasion machine.
How modern scam callers engineer trust and urgency
Today’s phone fraud is a stage play of credibility. Callers open with crisp identification, drop a plausible case number, and mirror details you’ve leaked online to make it feel “account-specific.” They spoof a local or official caller ID, route you through a fake transfer to a supervisor, and use curated hold music to signal enterprise polish. Some even mimic known voices with AI cloning, sprinkle in micro-facts (your city, ISP, last four digits of a non-sensitive ID), and perform “security rituals” like reading a policy disclaimer to lower your guard before the ask.
- Legitimacy cues: spoofed numbers, formal scripts, ticket IDs, internal jargon
- Authority stacking: agent → senior agent → “fraud team” escalation
- Mirroring: repeats your words and context to create rapport
- Breadcrumb data: harmless facts to imply deeper access
- Interactive validation: “I’ll wait while you check” to seem patient and real
- Voice polish: confident tone, steady pacing, credible silence and typing sounds
Once the facade holds, they shift gears to compress your decision window. You’ll hear about an “active breach,” a time-limited lock, or a refund error that “must be reversed now.” They isolate you with “stay on the line, don’t call anyone,” inject countdowns, and direct you through rehearsed steps: open email, read a 2FA code, install a remote-access app, move funds to a “safe” account. The pressure isn’t random; it’s engineered to bypass deliberation and trigger compliance before doubt can form.
- Countdown pressure: “Account closes in 10 minutes”
- Isolation play: “Don’t talk to your bank; this line is secure”
- Procedural sprint: rapid-fire instructions to keep you reactive
- Escalation threat: legal action, payroll holds, shipment seizure
- False fixes: bogus “safe wallet,” gift cards, cashier’s deposits
- Code capture: requests to “verify” by reading your one-time passcode
| Red flag phrase | What it signals | Safer move |
|---|---|---|
| “Read me the code we just sent.” | 2FA theft | Never share codes; end call and contact the org via the official site. |
| “Stay on the line-don’t call anyone.” | Isolation tactic | Hang up; dial the published number on your card or bill. |
| “Install this tool so I can help.” | Remote-control setup | Refuse remote apps; consult a trusted local technician. |
| “We overpaid your refund-send it back now.” | Money mule pressure | Check your bank independently; ignore payment instructions. |
Proof points to demand before sharing any information
Before answering a single question, shift control back to you. Require the caller to provide verifiable evidence that can be checked through an independent, official channel you choose. Favor proofs that you can confirm using a website you type yourself, a number printed on an official statement, or an app you already use. Anything that can’t survive a channel switch or a time delay isn’t real assurance-it’s a script.
- Official callback path: Ask for their name, department, and case topic-then hang up and call the organization’s published main number to be transferred back.
- Reference or case ID: Demand an ID you can verify via the company’s website or app, not a link they text or email to you.
- Employee verification: Request an employee ID and internal extension that the main switchboard can confirm.
- Channel-consistent contact: Insist on a message in your existing secure portal or app inbox; no “one-off” emails, links, or attachments.
- Purpose clarity: Require a clear, non-sensitive reason for the call and what specific policy or incident triggered it.
- No-rush window: Legitimate agents allow time for verification; pressure, countdowns, or threats are automatic deal-breakers.
Use a simple cross-check: independent source, controlled channel, and time buffer. If any leg fails, stop. The quick matrix below shows what to ask for, why it matters, and how to validate without exposing personal data.
| Ask For | Why It Matters | How to Verify |
|---|---|---|
| Agent name & employee ID | Ties caller to a real org record | Call main number; request transfer and confirm details |
| Case/reference ID | Creates an auditable trail | Check in your official app/portal you open yourself |
| Callback via published line | Breaks spoofed caller control | Use the number on your card, bill, or website footer |
| Written follow-up | Allows time to assess | Read only messages inside your known account inbox |
| Specific policy or incident | Filters vague scare tactics | Ask for the policy name/ID; confirm on the site’s help center |
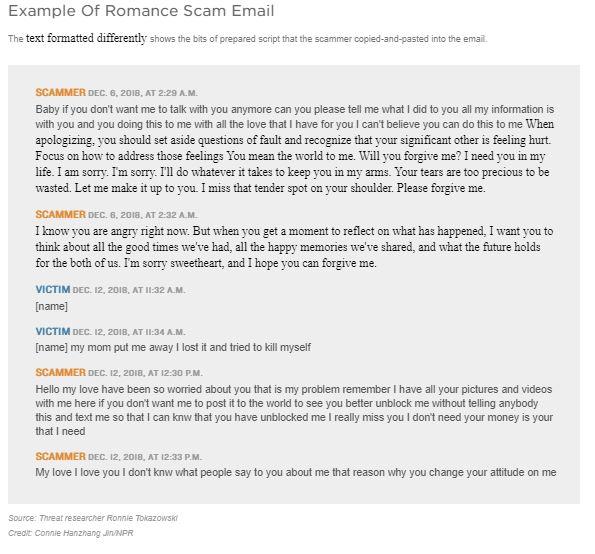
A practical script to respond document and refuse
Use a calm, assertive script that buys time, gathers verifiable details, and ends the call on your terms. Speak slowly and pause often so the caller fills the silence. Keep your identity private, flip the verification burden, and ask for documentation you can review independently.
- Hello, who am I speaking with? Please spell your full name and department.
- Company and purpose: Which organization are you calling from, and why?
- Send it in writing: I don’t confirm information by phone. Email or mail official documents to the address on my account.
- Verification: What is your callback number, website, and case/reference ID?
- Privacy: I will not share codes, PINs, or personal data. If this is legitimate, you can proceed via written notice.
- Boundary: I’m ending this call now. Remove my number from your list. Goodbye.
Immediately after, record what happened and report it. Keep entries short and factual; never click links or call back numbers given during the call-use official contact channels you already trust. Block the number, monitor accounts, and if any information was disclosed, change passwords and enable multi‑factor authentication.
| Time | Caller ID | Claimed Org | Pitch/Threat | My Action | Reported To |
|---|---|---|---|---|---|
| 10:32 AM | +1 555‑0142 | “Your Bank” | Account locked | Refused; asked for docs | FTC, Bank |
| 6:18 PM | Unknown | Utility | Immediate disconnection | Ended call; blocked | State AG |
| 8:05 AM | +44 20 7946 | Tech Support | Virus on device | No info shared | Platform report |
Post call checklist for reporting blocking and identity protection
Capture evidence before it disappears: take a screenshot of the call log and any voicemail transcript, and jot a one-line summary of what was said. Don’t call back unknown numbers, even if the caller ID looks local-scammers spoof area codes to bait returns. Lock down your phone’s protections so repeats get filtered instead of answered, and make sure your device and carrier settings are up to date for the latest blocking features.
- Document: number, timestamp, caller ID name, and the “ask” (money, codes, account access).
- Block and label: Phone app > Recents > Block/Report; add to device and carrier block lists.
- Filter: enable Silence Unknown Callers (iOS) or Caller ID & Spam Protection (Android).
- Report SMS: forward phishing texts to 7726 (SPAM) if supported by your carrier, then delete the thread.
- Update: install OS/security updates; check carrier’s spam tools or apps are enabled.
If any personal details were shared, move quickly to reduce risk. Reset passwords-starting with email and banking-enable 2‑factor authentication, and watch accounts for unusual activity. Consider a fraud alert or credit freeze if sensitive data was exposed, and file official reports so patterns are tracked across networks.
| Action | Where | Why |
|---|---|---|
| Report number | Carrier app or code (e.g., 7726) | Flags it network‑wide |
| Regulator report | US: reportfraud.ftc.gov; UK: Action Fraud; AU: Scamwatch | Enables investigations |
| Device block | Phone > Recents > Block/Report | Stops repeat calls |
| Fraud alert/freeze | Credit bureaus | Prevents new accounts |
| Secure accounts | Password reset + 2FA | Limits takeover risk |
- Monitor: enable bank/card alerts; review statements and login history.
- Revoke access: sign out of all sessions; remove unknown devices/app passwords.
- Escalate: contact your bank if you shared codes or transferred money; keep case numbers.
Concluding Remarks
In the end, a scam call is just another voice trying to borrow your certainty. The best countermeasure isn’t fear-it’s friction. A pause. A check. A habit of verifying before you react. Let unknown numbers go to voicemail, call back through official channels, and treat urgency as a cue to slow down, not speed up.
If something feels off, document it and report it to your phone carrier and the relevant consumer protection bodies in your area. Share what you’ve learned with friends and family without blame; today’s targets are often yesterday’s teachers.
The phone will keep ringing. Some calls will matter, many won’t, and a few will try to play the part of trust. Keep your number, keep your calm, and keep your processes. That way, when the line crackles with doubt, you’ll know exactly when to hang up-and when to pick up with confidence.
